Scalable Granular Data Entitlements with Redshift RLS and TrustLogix
Stay in the Know
Subscribe to Our Blog
Earlier this summer, Amazon announced Redshift RLS (Row Level Security) , a rich new set of capabilities that ease much of the manual work needed to implement fine-grained data access control. This allows Redshift customers to much more easily manage complex data security use cases that mandate tight control over the users and roles that are allowed to access specific rows in organizational data sets.
Fine-Grained Entitlements Use Cases
Use cases for fine-grained access control span just about every key industry vertical and are needed for organizations ranging from high-growth startups to global enterprises.
- Only people responsible for managing specific customer accounts can see data for those customers
- Only caregivers for a particular patient can see that patient’s medical record
- Individual contributors can see their own payroll data and managers can view payroll data, but only for their team members
Combined with the existing Redshift Column-Level Access Control features, customers can now tighten the scope of their data access control further such that:
- Account managers can see customer purchase information for their customers, but they cannot see the customer’s financial information (limited to the Finance and Accounts Receivable teams)
- Doctors and nurses can see their patients’ healthcare information, but not their billing information
Watch: Amazon Redshift RLS Launch Announcement Keynote (featuring TrustLogix)
The customer benefits that RLS delivers by enabling these use cases are obvious. However, customers still have to write complex SQL code to model policies and manage those policies across multiple Redshift clusters. Addressing these and other challenges discussed below will help customers deploy at scale and maximize the benefits they get with RLS.
Deployment-at-Scale Challenges
Here are some of the additional challenges customers still need to contend when deploying RLS.
- Manual SQL Coding of Policies – RLS policies still need to be defined in SQL code, which creates challenges at multiple levels. Customers need to ramp up additional security staff that is trained on RLS to ensure that policies are correctly implemented in line with what the business mandates.
- External User Attributes and Custom Entitlements – Large organizations, particularly in financial services, have extremely sophisticated business rules about data access that incorporate user attributes and codify complex relationships in external systems. These too have to be manually coded into policies.
- Consistency Across Multiple Redshift Clusters – These policies need to be hand-coded consistently across multiple Redshift clusters. Even in simple deployments, it’s very likely that customers will have Dev, Test, and Prod environments where these policies must be applied consistently to ensure both quality and security.
- Multi-Cloud Scalability – Many of our joint AWS Redshift clients have data spread across additional data stores such as Snowflake and Databricks, and they need to ensure that the same business policy is expressed correctly across the various security controls that each of those vendors has built into their platforms
- Auditability – Finally, customers need to ensure that they are still enforcing the Principle of Least Privilege, Segregation of Duties (SoD), discovering Dark Data, and ensuring compliance with legislative drivers such as GDPR, CCPA, HIPAA, and SOX
TrustLogix Scales Data Entitlements with Redshift RLS
Through our partnership with AWS, TrustLogix was invited to the RLS private beta and had the privilege of working with the Redshift development team pre-release to deliver a rich, high-quality integration that helps joint customers scale their RLS benefits further by addressing these gaps. Those benefits are recapped below, and are expanded on in our recent guest post on the AWS Big Data Blog.
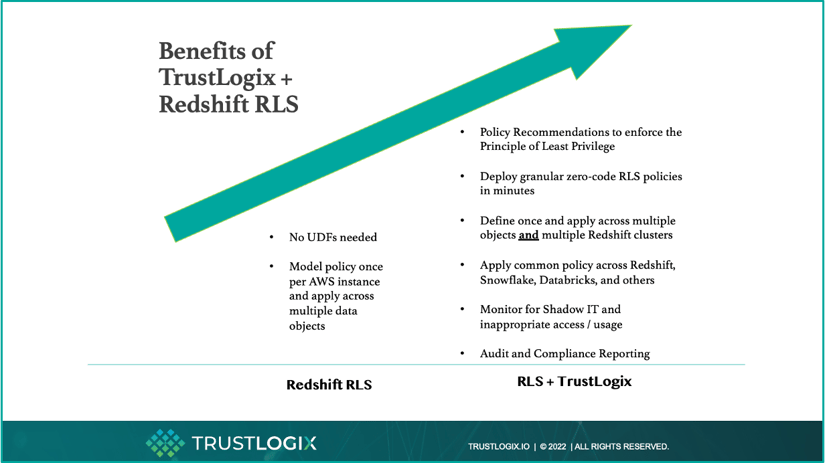
- No-Code Policy Management: Data owners and security teams express their business policies from the TrustLogix console, and our platform then generates and deploys the appropriate SQL code to create and enforce the corresponding RLS policy
- ABAC (attribute-based access controls) Policies: Security teams incorporate user roles and attributes as well as relationship data from existing customer databases directly into their granular policies directly from within the TrustLogix console, and again the platform generates the requisite SQL code for the corresponding RLS policy
- Consistency Across Redshift Clusters: Once the policy is modeled within TrustLogix, it can be uniformly applied and managed from a single pane of glass across multiple Redshift clusters (e.g. Dev, Test, Stage, Prod)
- Scale Across Multiple Clouds: Because TrustLogix has deep integrations with other data platforms like Snowflake and Databricks, the same policy can now be universally applied across multiple clouds
- Full Auditability: TrustLogix constantly monitors Redshift and other data platforms to look for Dark Data, Overprivileged Access, and to ensure compliance with GDPR, CCPA, and other legislative mandates
Read: Identify Blind Spots in Your Cloud Using Data-Centric Security
Amazon Redshift RLS has delivered powerful Data Entitlements capabilities for its customers. The TrustLogix integration with this new capability empowers our joint customers to maximize the benefits that they get from this powerful feature set.
![]()


