TrustLogix
Product Tour
Distribution and fragmentation of data across multiple data platforms and clouds has made it more challenging than ever to deliver the right data to the right people at the right time, safely and securely.
Through these four simple steps, TrustLogix helps you quickly and easily overcome this challenge and become your organization's Data Hero.
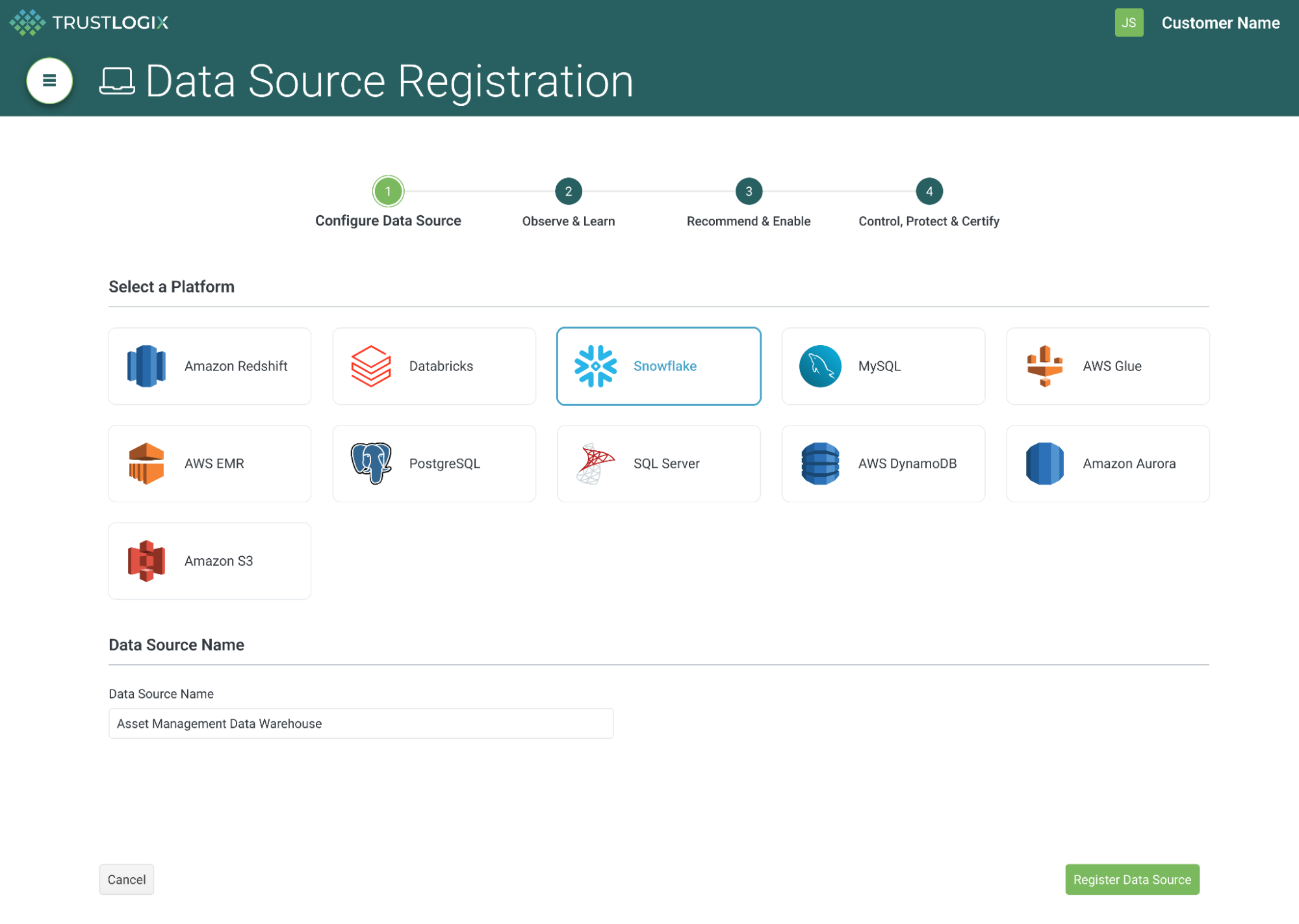
Overcome Distribution & Fragmentation of Data
Through 4 Simple Steps
Observe & Learn
Discover sensitive data access issues and risks.
TrustLogix automatically and continuously observes data usage patterns, identifies "dark data," and discovers access control issues, such as overly granted access and "ghost" or unused user accounts. TrustLogix achieves this non-invasively, without proxies, agents, or changes to your data, and without needing visibility to the data itself.
Recommend & Enable
Define data access roles and policies.
Once you understand your sensitive data issues and risks, you can define policies to address them. TrustLogix simplifies this by providing actionable recommendations for the full spectrum of issues and risks, including:
- Curtailing dark data and data sprawl
- Changing or defining new access policies
- Specifying authorized clients
Control & Protect
Deploy policies and provide visibility to your data security posture.
Once defined, your policies can be deployed to their target data platforms, including fine-grained attribute-based access control (ABAC) and role-based access control (RBAC) policies. TrustLogix leverages these platforms' native functionality, thus does not require any additional configuration or deploying any additional code to the data platform.
Audit & Certify
Continuously monitor, report, and alert on data access issues & risks.
TrustLogix continuously monitors and alerts for new risks and non-compliance such as suspicious activity, over-privileged accounts, ghost accounts, and new dark data or data sprawl, thus empowering you to respond quickly and decisively to address them. Additionally, alerts can be reported to SIEM and other GRC systems.
A Practical Methodology to
Secure Your Cloud Data
Download our latest guide on how to protect your cloud data.

SEE FOR YOURSELF HOW WE CAN HELP YOU




