Identify Blind Spots in Your Cloud Using Data-Centric Security

Most enterprises are migrating to Cloud data platforms to gain insights from and monetize their data. As sensitive data is moved to the cloud and across disparate data platforms such as data lakes, data warehouses, and data analytics tools, it creates “blind spots” – pockets of data and data stores that have slipped through the cracks in your control plane, creating cost and risk for your organization.
Enterprises need a new data security model – a model that effectively adapts to the complexity of the modern multi-cloud, multi-data platform architecture, monitors and protects data wherever it is located. The model should empower Data Operations teams to provide data to data consumers in a fast and secure way.
The key for this model to work is Data-Centric Security. This approach relies on increased data security, easily demonstrable compliance, increased speed of anomaly detection and remediation by continuously monitoring data access patterns and adjusting the security posture.
The TrustLogix Data Security Governance platform aligns with many of the key tenets of Zero Trust architecture conceptualized by NIST 800-207 to monitor the integrity and security posture of modern cloud Data platforms. The following key capabilities are provided in the TrustLogix platform:
- Visibility and audit reporting
- Identification of Dark data
- Usage of Shadow IT and non compliant tools
- Detect overly granted access policies
- Detect Anomalous data access activities
Visibility and Audit reporting
TrustLogix provides easy to use reports on various data access activities by users across multiple data platforms. Customers get complete visibility of historical data access patterns and data security permission assignments.
Some of the key use cases the TrustLogix platform reports on are:
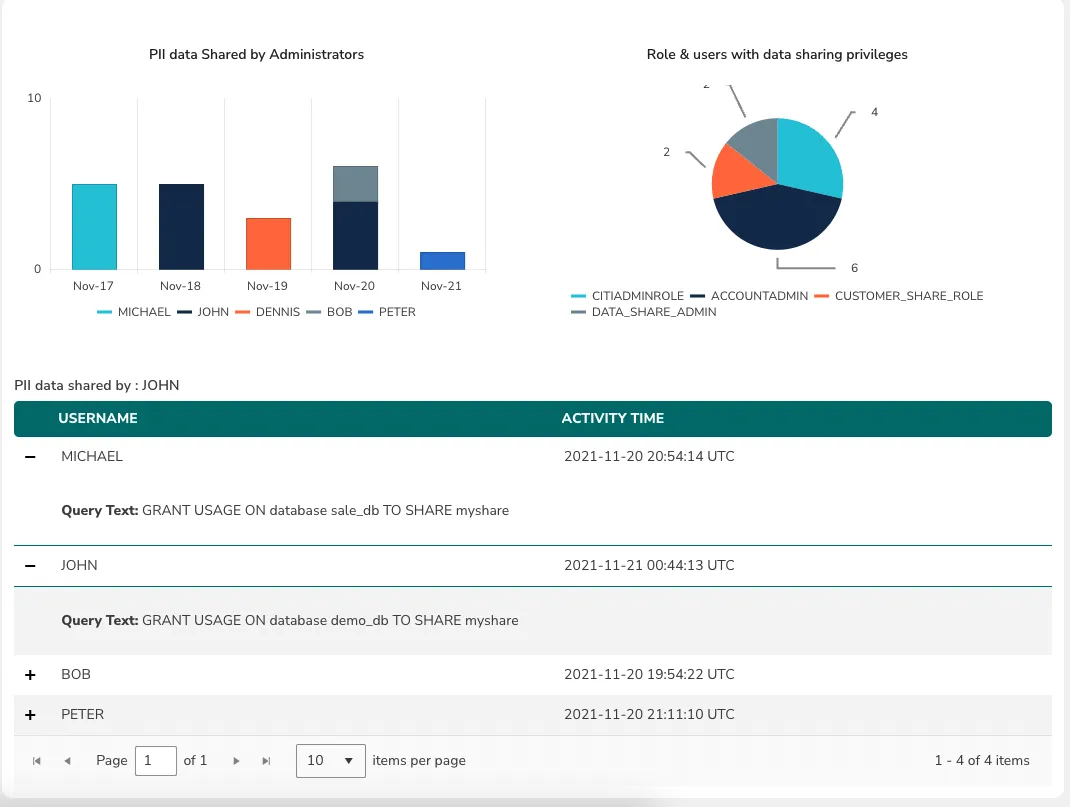
- Data access patterns by privileged Administrators vs end-users as well as the specific queries that were executed
- Data Sharing activities within the organization and with external partners or Data marketplaces
- Visibility of data sharing activity by users who have Administrator roles
- Visibility into data security configurations that can compromise the data, for example: enabling default Public role access to sensitive data
Why is this Important?
One of the principles of data-centric security is to understand how data is being accessed. By getting deep visibility into data usage, you gain many security and compliance benefits right off the bat:
- Identify over-privileged users and roles that create threat surfaces which expose your organization to unnecessary risk
- Understand where you’re not following the Principle of Least Privilege
- Identify Key Risk Indicators in your data security configurations that might expose your data
- Provide comprehensive audit reports on who has access to sensitive data for various regulations like SOX, GDPR, etc.
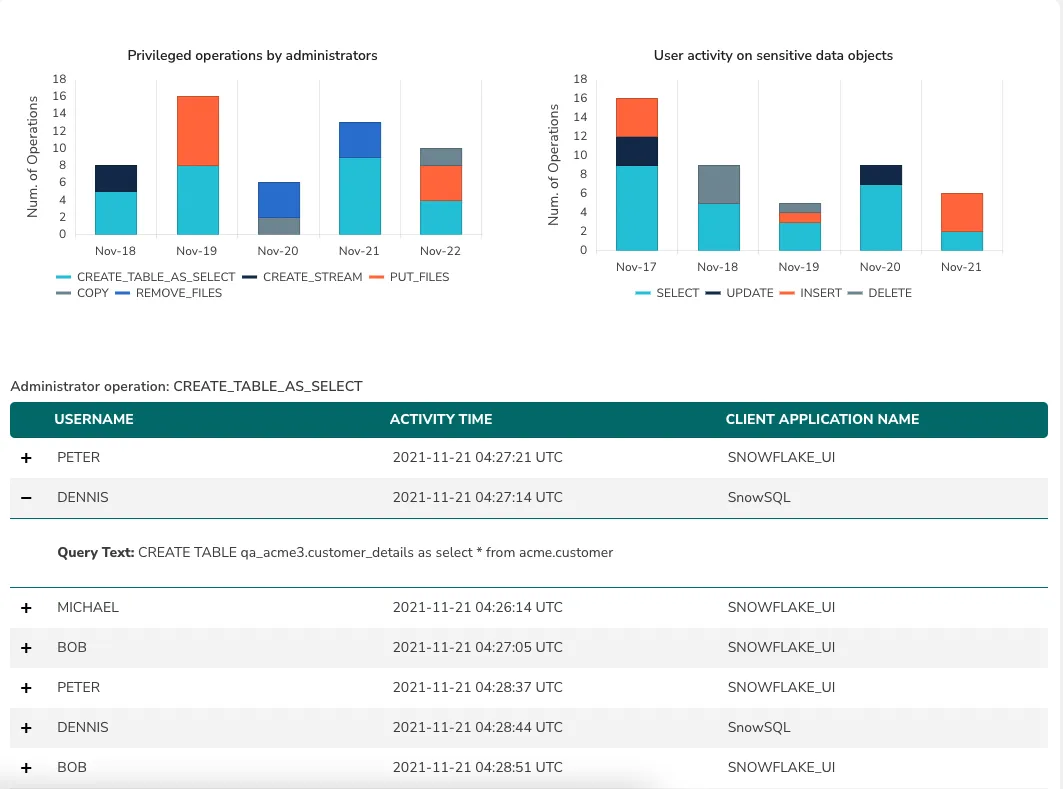
Discovery of Dark Data
As enterprises use different data platforms for their OLTP, data warehousing, analytics, and machine learning use cases, a vast amount of sensitive information moves across these platforms. This data frequently remains unused or orphaned after initial usage.
For instance, the QA team may create or copy an instance of a customer data set for testing purposes and this data is left unaccounted for after its initial usage. Or financial data may get moved to the cloud in anticipation of a new reporting app that never ends up getting built, and this data is never “retired” from your cloud repository.
The TrustLogix platform continuously monitors the entirety of your cloud data across your various platforms, tracking when they were created and by whom, and how frequently and recently they were accessed. TrustLogix's intelligent monitoring platform uses AI to provide actionable recommendations to effectively manage the lifecycle of sensitive data.
Why is This Important?
Dark Data can lead to numerous problems for an organization:
- Compliance violations: Regulations like GDPR require that all customer data must be deleted upon request and if there is customer data in your Dark Data pools, you could be inadvertently violating these mandates
- Data breaches: As this data is now left unprotected, it can lead to any malicious or unintended exposure if it’s not being tracked and removed if no longer needed.
Detect Overly Granted Access
The Principle of Least Privilege is as important to data as it is to your infrastructure and applications. This should be applied to your data-centric security model to reduce unauthorized access to data by limiting privileges to only users / identities as required by their job.
With enterprises storing an unprecedented amount of data in multiple cloud data platforms and with various consumers accessing this data, managing privileges is a huge task.
TrustLogix analyzes various access patterns and compares them with permissions and role assignments to determine which users have been overly granted access. This is a continuous process where we provide recommendations to refine the permissions at frequent intervals to achieve and maintain a least privilege access principle.
Why is This Important?
Typically, to reduce the friction between data consumer and producer teams, enterprises start by granting highly permissive roles. Ineffective data access controls can lead to compliance violations, overly exposing sensitive data, and malicious insider access.
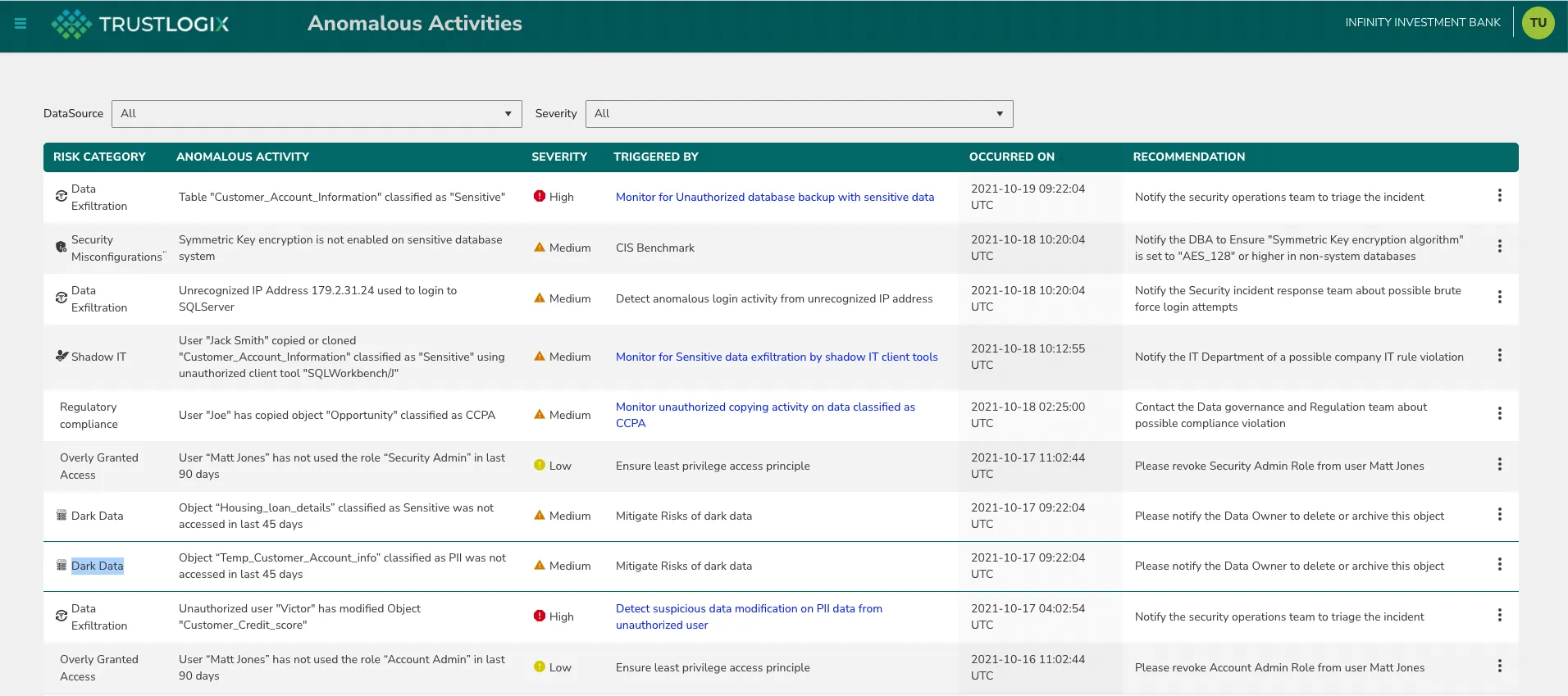
Anomalous Data Access Activities
Lastly, another important principle in Zero-Trust Data-Centric Security is to automatically identify anomalous activity and mitigate risky behavior. These activities tend to be highly correlated with malicious behavior and need to be analyzed in near real-time to reduce the risk of a data breach.
TrustLogix uses advanced machine learning algorithms to analyze various data access patterns, and privileged user activity to determine possible deviations from baseline activity.
Some of the critical incidents we look out for are:
- Users accessing sensitive data from previously unknown geo locations,
- Excessive number of sensitive data copy operations by users who have not previously done this
- Privileged Admin users copying private keys that encrypt the data
- Anomalous Data Sharing activities by Account administrators
Why is This Important?
With rapid growth and spread of data, enterprises need an incident detection system that is reliable and reduces alert fatigue. More than 80% of data breaches happen because of malicious or unintended insider activity . Enterprises require a platform that recognizes this anomalous activity by understanding data access patterns.
In summary, organizations require a modern solution that continuously monitors data access patterns to achieve a data-centric security solution for Cloud based data Platforms. The legacy methods of monitoring and protecting perimeter and not monitoring the data will expose them to potential business risks, data breaches and compliance violations.
To learn more about TrustLogix Cloud Native Data Security Governance please contact us for a demo of the solution or access the service from the AWS Marketplace.
Stay in the Know
Subscribe to Our Blog






