Visibility Monitoring and Protection of a Major Investment Bank’s Data in Snowflake
Stay in the Know
Subscribe to Our Blog
Brief Customer Introduction
The customer is a leading global, full-service investment banking and capital markets firm, with approximately $10B in annual revenue. Over the last several years, it has embarked on an enterprise-wide data modernization journey, which included moving a substantial portion of its operational and analytical workloads to the Snowflake Data Cloud.
Journey from OnPrem to Snowflake Cloud
The bank had chosen Snowflake as its enterprise-wide cloud data warehouse. As part of this journey, one of the main requirements was Data Security Posture Management: ensuring proper data security guardrails were in place, and having visibility to monitor and report on those guardrails. This required a solution that could monitor and alert on various anomalous activities across all Snowflake instances, including the following:
• Track Behavior of Privileged Users and Roles
• Alert on Anomalous Large Data Movement
• Monitoring Access to Sensitive Data Objects
• Alert on Repeated and Multiple Failed Logins
• Log and Alert on Account Control Commands like Assigning AccountAdmin, SecurityAdmin and UserAdmin Roles
Furthermore, as multiple business units were planning to migrate data into Snowflake, the CISO organization wanted visibility on what type of data is coming into Snowflake from upstream and being consumed by downstream tools. In other words, they wanted a holistic view of their entire Snowflake data ecosystem, and how that data was being accessed throughout the organization.
Challenges & Requirements
Their previous toolset was focused on traditional on-premise data sources and required setting up proxies and agents that monitored network traffic between data platform and data consumer. These tools were not built for cloud data sources and workloads that are serverless and scale up and down with demand, and they added an unacceptably high performance overhead. Additionally, these tools required routing of the actual data through their proxies and agents in order to manage data access and redaction, adding to the complexity of their data architecture and adding a potential threat vector if those tools were compromised (such as “man in the middle”). The security team required a solution that was natively built for cloud data platforms, was non-invasive to underlying data platforms and pipelines, and could not see or touch the data itself.
Another key requirement was to ensure that data democratization and collaboration was possible across the entire organization, without increased risk of data breaches or improper data sharing, and without these data security measures becoming a bottleneck for users being able to access the data they needed. They wanted to make the process of defining access policies and granting access to be as templatized and automated as possible, so data provisioning would continue to be fast and simple regardless of how many users and teams were being onboarded.
Additionally, as more lines of business (LOBs) were onboarded, they also required visibility of what tools were connecting to Snowflake and what data was moving into Snowflake and leaving it through various channels.
Finally, they wanted immediate visibility to whenever certain data security gaps emerged, including:
- Are there any users with overly granted permissions, which can lead to data leakage?
- Are there any ghost accounts that can be mis-used and lead to potential compliance violations?
- Is there any Dark Data that was brought into Snowflake and not being used?
- Are there any unapproved or non-whitelisted tools connecting to Snowflake, which can lead to data getting copied to unmonitored locations?
How TrustLogix Is Helping
Built as a cloud-native solution and designed so it cannot see or touch the data itself, TrustLogix provides a Data Security Posture Management service for Snowflake and various other cloud data platforms. The CISO team quickly implemented TrustLogix to monitor their Snowflake account to get insights into various types of risks.
Data risks are categorized into multiple categories: Dark Data, Data Exfiltration, Overly Granted Access, Regulatory Compliance, Shadow IT, and Misconfigurations.
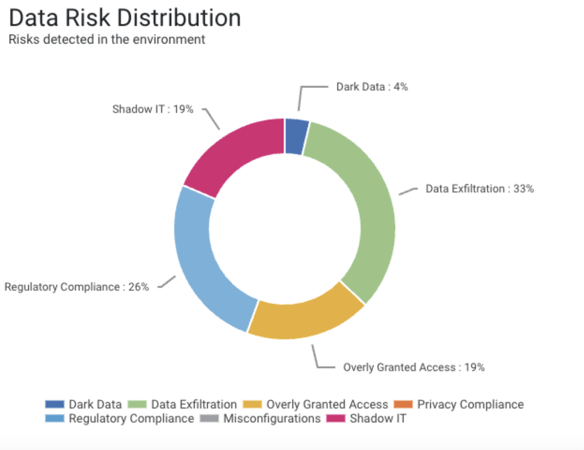
Each identified data risk in TrustLogix has an associated recommendation and a remedial action. These data risks and remedial actions are then funneled from TrustLogix to a SIEM system to make them actionable by the respective Data Owners or a Security point of contact. This integration reduced the friction between Security and Data teams and helps resolve any potential risks in an expedited manner.
Tracking Data Sprawl and Alerting on Anomalous Activities
The CISO organization required visibility into what data was moving into Snowflake and what was leaving. With its rich integration capabilities, Snowflake makes it easy for Data teams to connect with various tools for ETL , Data Analysis, ML/AI, or Data Visualization. If not appropriately managed, some of these tools can potentially move sensitive or company confidential data out of Snowflake in an unapproved manner, leading to data leaks and compliance violations.
TrustLogix provides a near real-time graphical view on what tools are connecting to Snowflake, what data is being moved, and the associated risks.
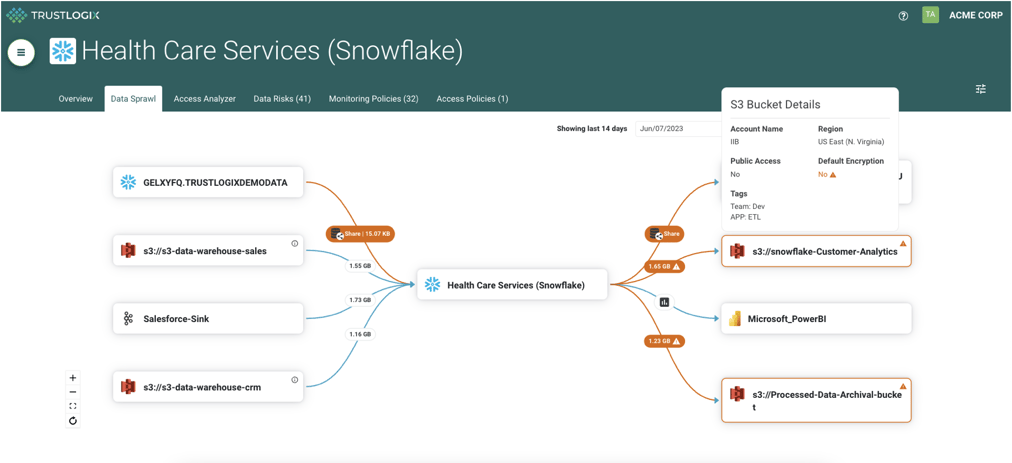
Data Sharing Between Snowflake Accounts
Additionally, the data teams share their data from production to development accounts for machine-learning model training. TrustLogix provides instant visibility on what type of production data is shared and identifies if there is any PII or confidential data that is shared without de-identifying it.
How TrustLogix Leverages Snowflake Data Clouds’ Built-In Capabilities
TrustLogix provides all this visibility without seeing or touching the data itself. TrustLogix achieves this by using only native functionality provided by the underlying data platforms. Access control policies are defined by TrustLogix, which in turn pushes down those policy definitions into Snowflake, and Snowflake itself then natively executes and enforces those policies. Also, TrustLogix integrates with Snowflake Account Usage views and logs to analyze data access patterns and derive key insights and data risks. As a result, only Snowflake sees and touches the data.
With these key capabilities in hand, the data teams and the CISO organization can facilitate faster adoption of Snowflake across the firm in a secure and compliant manner.
Want to learn more about how TrustLogix can help you democratize your data, safely and securely? Get a free data security audit and start identifying your data access issues within minutes, without TrustLogix ever seeing the data itself.
