TRUSTLOGIX FOR AWS REDSHIFT

Visibility, access governance, and audit across AWS Redshift clusters from a single pane of glass
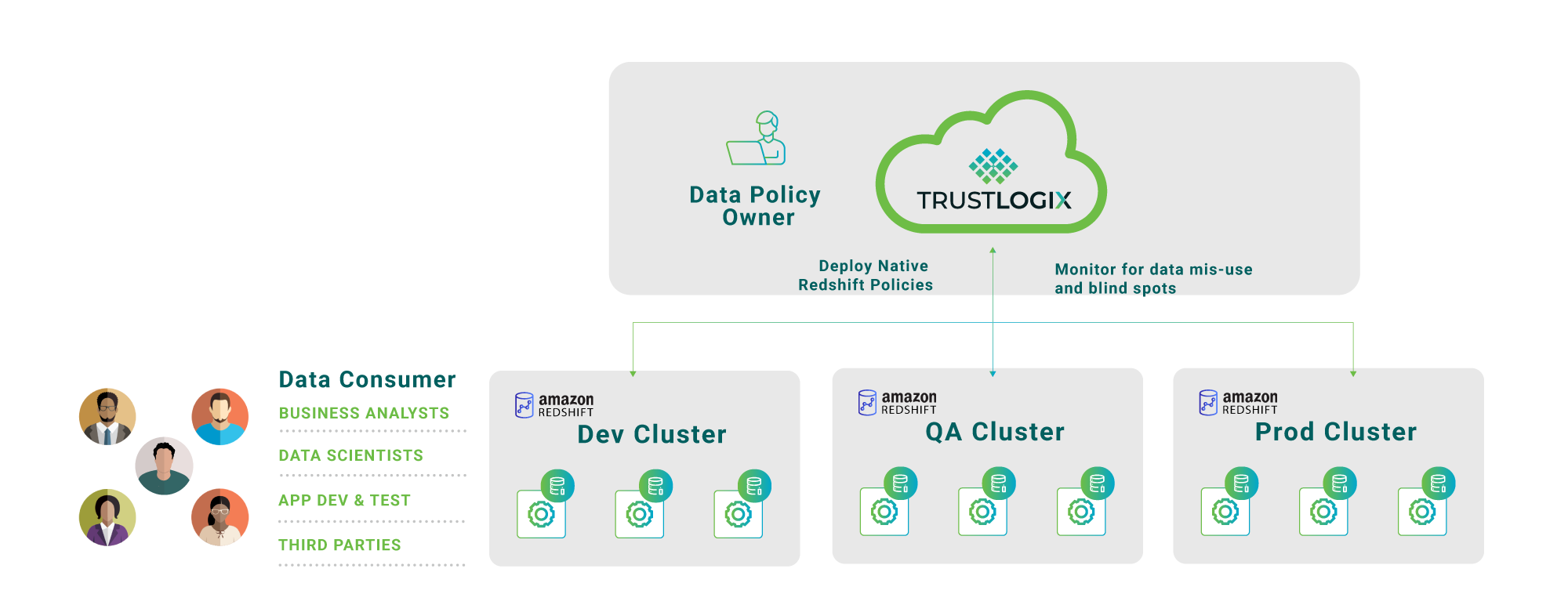
Secure, Govern, and Audit Transactional Data Access in AWS Redshift
TrustLogix helps organizations detect risky behavior, enforce fine-grained access, and ensure compliance across all Redshift environments.
Total visibility
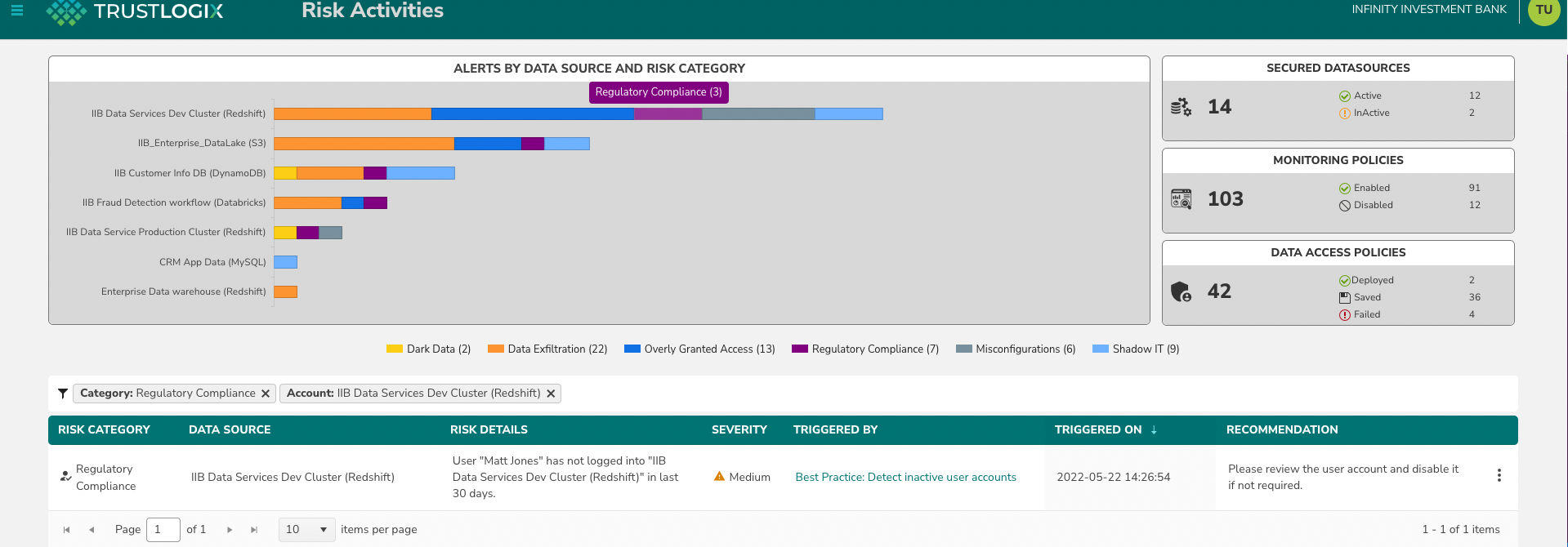
TrustLogix gives you a birds-eye view across all your Redshift instances, and detects over-privileged users and anonymous behavior that could indicate data exfiltration attempts
Actionable insights
TrustLogix analyzes Redshift data usage patterns and makes recommendations on how to tighten your data access governance policies to eliminate overly granted privileges and reduce risk

RBAC Integration
TrustLogix's RBAC integration enables seamless data entitlements policies by leveraging AWS IAM Roles directly from the TrustLogix console
RLS Integration for Row-Level Security
TrusLogix integrates with Redshift RLS to deliver fine-grained row-level security for your sensitive data
Column Masking for Privacy Mandates
Mask sensitive Redshift data like account numbers, credit cards, and other PII and PHI to cmply with legislative requirements like HIPAA, PCI, and GDPR
Codify Business Rules as Data Entitlements
The TrustLogix-Redshift integration lets you model business rules as fine-grained data entitlements directly from the TrustLogix console

Track Data Flow To and Through Redshift
TrustLogix lets you track how upstream data is consumed in Redshift and alerts you if it gets moved in anomalous frequencies or volumes
Enforce Policies Downstream
TrustLogix enforces your fine-grained Redshift policies even if your data scientists and analysts repackage third-part data into new products and services, and regardless of how consumers connect to Redshift to access that data
Honor Upstream Data Governance Mandates
TrustLogix enforces data access requirements in Redshift from upstream sources to ensure you're complying with SLAs and terms of use
Running in Minutes, Productive in Hours
You can be up and running, and productive with TrustLogix in just a few hours
Step 1
Step 2
Step 3
AWS Services supported












