Leveraging TrustLogix to Uphold Your End of Snowflake's Shared Responsibility Model with CIS Benchmark Alignment


Your Security Responsibilities Under Snowflake’s Shared Responsibility Model
Snowflake's cloud data platform enables enterprises to efficiently store and analyze massive amounts of data. However, securing data in the cloud requires shared responsibility between Snowflake and its customers. To assist customers in upholding their security obligations, Snowflake outlines its Snowflake Shared Responsibility Model for cloud security. It also has partnered with the Center for Internet Security (CIS) to publish prescriptive benchmarks and best practices for hardening and controlling Snowflake environments. TrustLogix provides solutions to help customers implement these security controls across their Snowflake instances. TrustLogix delivers monitoring and visibility into Snowflake security configurations, activity logs, and IAM data, supporting customers in fulfilling their shared responsibilities.
CIS Benchmark Controls for Snowflake
The CIS Benchmarks for Snowflake offer a comprehensive set of recommendations to securely configure Snowflake environments. The Benchmarks encompass controls across several critical areas:
- Identity and Access Management — Includes guidance on multi-factor authentication, password policies, least privilege access, and separation of duties.
- Monitoring, Auditing, and Logging — Provides directives on enabling activity logging, monitoring log data.
- Network Security — Recommendations such as, VPN access, IP whitelisting, and TLS encryption for data in transit.
- Data Protection — Covers encryption at rest, key management, database firewalls, and data masking controls.
Based on the Snowflake Shared Responsibility Model, customers are responsible for following controls in each area
- Identity and Access Management — Managing entitlements, separation of duties, maintaining least privileged access and MFA for end users is the customer's responsibility.
- Monitoring, Auditing and Logging — Customers are responsible for log review, analysis and integration with SIEM platforms.
- Network Security — Customers must manage their privateLinks, VPCs, whitelisting of IP addresses, and encryption in transit.
- Data Protection — Masking of sensitive data, enforcing appropriate row access policies, encryption of data at rest, key management, are owned by the customer.
TrustLogix provides solutions to help customers automate these security controls across their Snowflake instances to maintain their end of shared responsibility.
Snowflake CIS Controls and TrustLogix
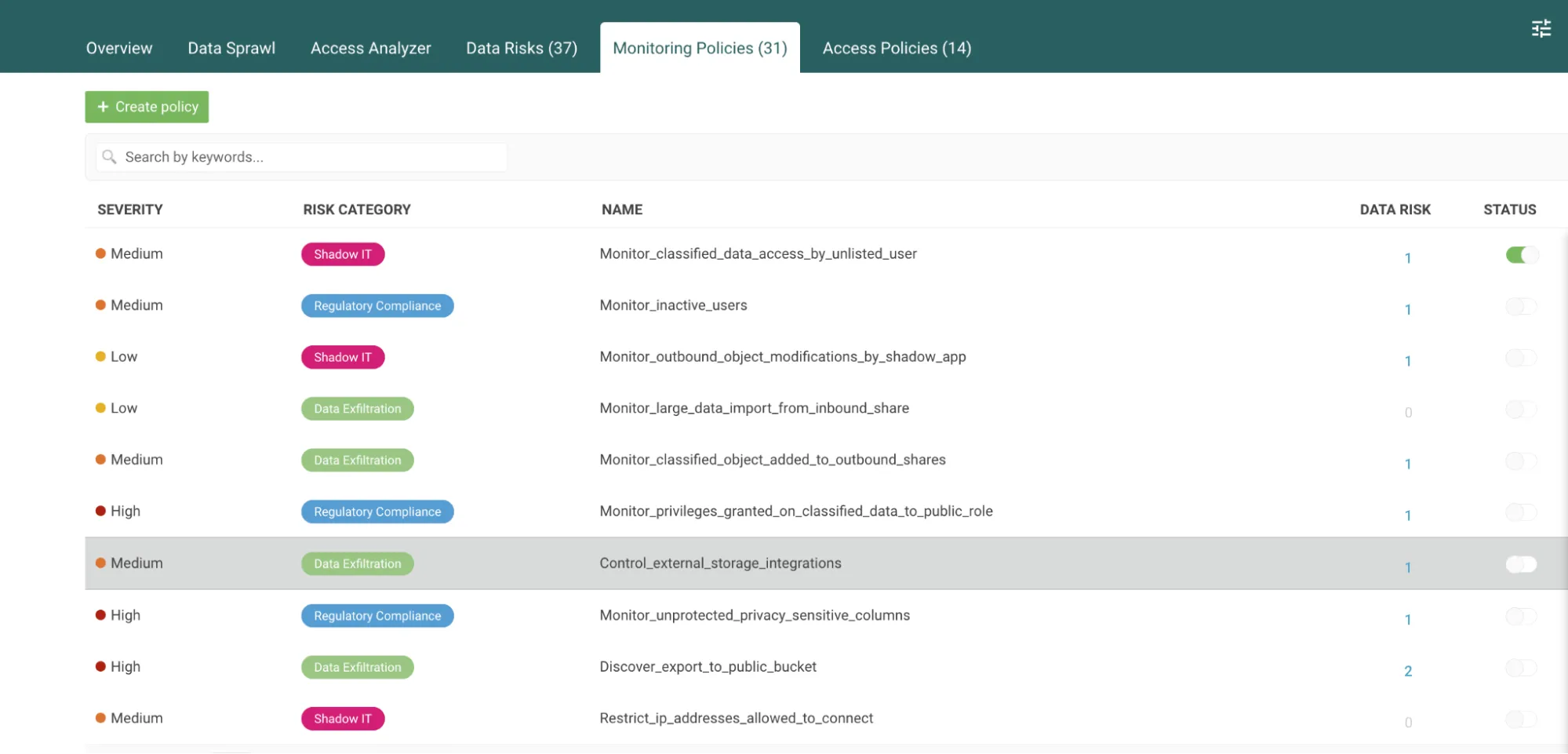
TrustLogix provides pre-built guardrail policies to ensure customers uphold their security responsibilities as outlined in the Snowflake CIS benchmarks. For example, TrustLogix helps monitor:
- Overly Granted Access
- Ensure system roles like ACCOUNTADMIN, USERADMIN, and SYSTEMADMIN are assigned only to a small number of users
- Verify no users have ACCOUNTADMIN or SECURITYADMIN set as their default role
- Improper Configurations
- Network level policies — Ensure that user-level network policies have been configured for service accounts
- Ensure that the PREVENT_UNLOAD_TO_INLINE_URL account parameter is set to true
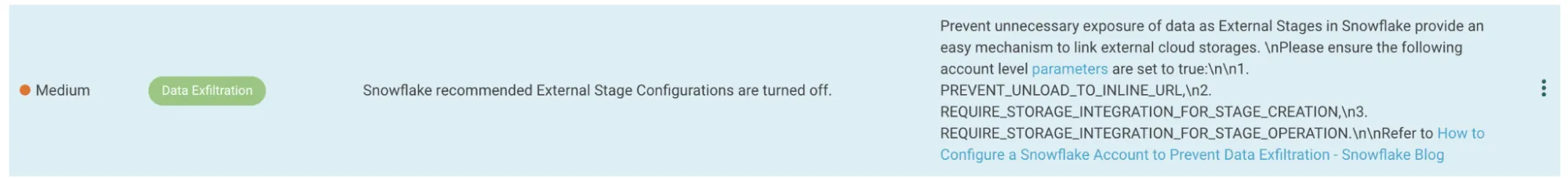
- Unprotected Sensitive Data
- Ensure that data masking is enabled for sensitive data
- Ensure that sensitive data is not being shared
- Monitor for data granted to Public Role

Explore How to Simplify Data Security and Privacy for the Snowflake Data Cloud
TrustLogix Monitoring and Visibility
Furthermore, TrustLogix provides a Data Security Posture Management service designed for Snowflake. TrustLogix continuously monitors Snowflake accounts to gain visibility into various data risk categories, including:
- Dark Data risks — Identifying unused data left unclassified or unprotected
- Data Exfiltration risks — Detecting abnormal data access or transfers
- Overly Granted Access risks — Finding improper user permissions and entitlement creep
- Regulatory Compliance risks — Spotting configuration gaps against frameworks like HIPAA and PCI
- Shadow IT risks — Discovering unsanctioned tools that connect to Snowflake instances
- Misconfiguration risks — Pinpointing security policy gaps or flawed settings
TrustLogix analyzes these risks to provide actionable intelligence for securing data within Snowflake environments. The solution integrates directly with Snowflake to provide automated access discovery risks and provide continuous insights into their Snowflake security posture across multiple risk factors.
Learn More about the Top 7 Cloud Data Risks
Summary
Snowflake delivers tremendous value by enabling enterprises to store and analyze massive amounts of data in the cloud. However, the shared responsibility model dictates that customers must take steps to secure their Snowflake environments.
As a Snowflake partner, TrustLogix offers customers a way to uphold their security obligations by providing continuous monitoring and visibility into their Snowflake posture. TrustLogix integrates with Snowflake to automatically monitor configurations, analyze access patterns, and detect risks.
With out-of-the-box CIS-aligned guardrails and actionable intelligence across risk categories like privileged access, data transfers, and misconfigurations, TrustLogix strengthens Snowflake security. Customers gain the tools and insights needed to identify and respond to security gaps in their Snowflake instance. By leveraging TrustLogix, enterprises can securely operate Snowflake while meeting their end of the shared responsibility model.
Stay in the Know
Subscribe to Our Blog






